Integration is often central to effective information governance. This includes integrated policies, processes, strategies, controls, and technologies. Some of the biggest obstacles to integration are often organizational silos[1]—separations of departments, people, and functions that can hinder the flow of information and how it’s managed. Bringing together two groups whose organizational silos may be impeding a meaningful relationship, however, can help improve the flow of information and its management. Information security (IS) professionals, meet records and information management (RIM) professionals. You two have a lot in common, and I think you could be great friends.
Why Information Security Professionals Should Partner with RIM Professionals
Reduce Risk by Disposing of Information When It’s No Longer Needed: One way to spark a RIM professional’s interest is to start talking about retention and disposition. Much like the downsizing and decluttering experts on the show Hoarders, RIM professionals want to eliminate ROT (redundant, obsolete, and trivial information). Their guiding force is an organization’s records retention schedule (RRS), which they no doubt have spent years calibrating to ensure that record series and retention periods reflect sound business needs, legal requirements, and best practices. To increase information security, IS professionals can cash in on the RIM professionals’ obsession with the RRS, retention periods, and proper disposition of ripe information. Every byte of information that’s defensibly destroyed chips away at risk. The less information an organization holds, the less information is available for an intruder to access. With data breaches skyrocketing in number and sophistication,[2] IS and RIM professionals might sleep better after working together to enhance defenses and reduce exposure to breaches.
Know What Information You Have to Assess How to Protect It: RIM professionals know company records and information. From the most routine project meeting notes to the organization’s most sensitive information, RIM professionals can help IS professionals know the what and where of the organization’s records and information. When information security is assessing the information that bad actors could target—such as customer, employee, payment card, financial, or health information—and strategizing about how best to protect it, RIM can help provide valuable metrics about information quantity and location. It is much easier for IS professionals to help secure an organization’s information when they know what information the organization has.
Don’t Leave Out Your Mutual Friend, Privacy: Possession of personal information—particularly sensitive personal information, such as health data—amplifies the potential consequences of inadequate planning and protection. As RIM and IS professionals work to break down the barriers that separate them, they should invite privacy along for the adventure. Privacy is very popular with regulators these days. RIM, information security, and privacy must cooperate in appraising, understanding, and protecting personal information. This will avoid a host of potentially dire consequences related to over-retention, breach, or other issues related to that information. As an icebreaker, ask where sensitive or confidential information is stored and what can be done to help limit its associated risks.
Why RIM Professionals Should Partner with IS Professionals
Identifying, Prioritizing, and Strategizing About Risk: IS professionals manage risk. From assessing potential hacks to implementing the cybersecurity threat lifecycle (Identify, Protect, Detect, Respond, and Recover), IS professionals think about risk a lot. RIM professionals can benefit from this knowledge. For example, information security can help RIM professionals vet RIM vendors, assess the risks of cloud versus onsite file storage, or ensure secure records retention systems. While day-to-day RIM processes aren’t as risk-driven as information security processes, RIM professionals still must think about risks. They could likely learn from IS professionals to help sharpen their thinking about risk.
Socialization and Training: Information security, and more specifically, its sub-discipline cybersecurity tends to be very visible in most organizations. The issues that cybersecurity professionals work to prevent involve threats to which any employee can fall victim. So focused socialization and training are important tools for teaching employees how to identify and avoid those threats. Given the significance of cybersecurity risks, many organizations dedicate similarly significant resources to cybersecurity socialization and training. Most RIM programs, on the other hand, receive fewer resources. This provides an opportunity for RIM professionals to enhance RIM-related socialization and training by collaborating with IS professionals about things that have worked well and things to avoid while building socialization and training programs. Cybersecurity experts also can help RIM professionals develop these programs. Discussion points can include guidance on ingraining processes into habits using a top-down and bottom-up approach, making the processes fun for employees, enhancing communication, and making it easy to do the right thing.[3]
Don’t Forgot Your Other Mutual Friend, Compliance: Speaking of top-down and bottom-up approaches, RIM and IS professionals also should become well acquainted with compliance. Collaborating on integrating policies, processes, training, and strategies are best practices for moving an organization toward what it should—or, if you have more firmly worded procedures, “must”—do with respect to information management. However, these steps alone often aren’t sufficient to change organizational behavior. One other risk and records management groundwork has been laid, compliance professionals, such as internal audit, can enforce controls and training requirements. Internal audit can also help ensure management (top) is setting a tone of compliance with RIM and information security policies and procedures and employees (bottom) are invested in the same, and help RIM and IS professionals respectfully address and reform non-compliance. As an icebreaker, ask about options for multiple safeguards to protect RIM and information security processes that you identify as the most critical or involving the most risk.
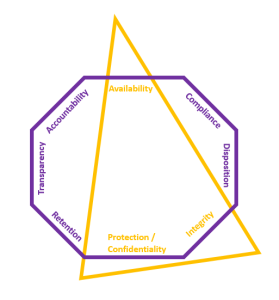
Even More Common Ground – Key Principles Align:
Information Security’s CIA Triad: Information security and, specifically, cybersecurity, look to the CIA triad—confidentiality, integrity, and availability—as a model for combatting threats.[4] Confidentiality entails restricting access to only authorized parties to prevent cyber-attacks; integrity ensures that data has not been altered from its original trustworthy form; and availability ensures that the correct parties can access the data when needed.[5]
ARMA’s Generally Accepted Recordkeeping Principles® (Principles): The CIA triad should look familiar to RIM professionals because it closely corresponds with three of ARMA’s Principles.[6] ARMA’s principle of protection requires that “an appropriate level of protection” is given “to information assets” based on the nature of those assets, and that appropriate security controls are established so that “only authorized personnel can access the information assets.”[7] Sounds like CIA confidentiality, doesn’t it? Similarly, ARMA’s principle of integrity requires “a reasonable guarantee of authenticity and reliability,” and availability requires “timely, efficient, and accurate retrieval.”[8] This all sounds very familiar!
Below is a (very Star Trek-esque) graphic that shows the overlap:
Overlap of ARMA Principles®[9] and CIA Triad:
Conclusion
RIM and information security are essential components of any organization’s risk and records management initiatives. And the two groups have so much in common with organizational purpose and responsibility and so much to gain from collaborating. It seems high time they escape their silos and properly meet. By working together with privacy and compliance, RIM and information security can help organizations better protect sensitive information, minimize the risk of security incidents, implement and enforce controls, and, overall, improve information governance.
[1] Jim Walery, Data Governance Breaks Down Silos (Data and Organizational), idata (Aug. 21, 2019), https://blog.idatainc.com/dg-break-down-silos
[2] Not “If” But “When”—The Ever Increasing Threat of a Data Breach in 2021, K&L Gates LLP (Jul. 15, 2021), https://www.jdsupra.com/legalnews/not-if-but-when-the-ever-increasing-8569092/
[3] “Cybersecurity – The Mile-High View for Records and Information Management Professionals” with guest presenters Dr. S. M. Loo and Elizabeth Khan, Zasio Virtual Coffee (Feb. 2, 2023), https://www.zasio.com/virtual-coffee-with-consulting/
[4] Id.
[5] Id.
[6] Implementing the Generally Accepted Recordkeeping Principles®, ARMA International (Aug. 13, 2017), https://www.arma.org/general/custom.asp?page=principles
[7] Id.
[8] Id.
[9] Id.
Disclaimer: The purpose of this post is to provide general education on Information Governance software topics. The statements are informational only and do not constitute legal advice. If you have specific questions regarding the application of the law to your business activities, you should seek the advice of your legal counsel.

